Inline Ethernet Tapping & Data Exfiltration
I usually have some crazy research ideas and like to run with them sometimes. In this experiment I have managed to tap the inline physical RX and TX (receive and transmission) wires of an ethernet cable of a target computer or system using sewing needles. This research experiment was not based off of anything I've seen as I couldn't find any related posts online at the time.
My first experiment consisted of stripping some of the target's RX and TX wire from the middle which is difficult to do without damaging the wire, although this was a quick way to prove that it could work. I soldered on the TX and RX wires of another ethernet cable and then connected that to an ethernet port relaying all of the target's network packets to the listening computer while the target system was still able to stay connected to it's network.
The Ethernet Cable

- The orange pair: this pair is used for transmitting data packets
- The green pair: this pair is used for receiving data packets
- Surprisingly the other blue and brown pairs are not used for data, although they may be used for PoE (Power over Ethernet) in some network configurations.
First Experiment
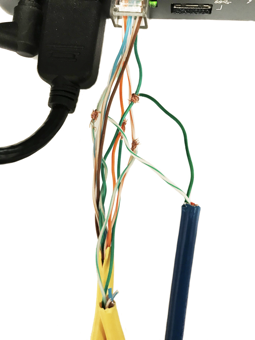
- You can see the listener's green RX wires wired into the target's TX - this is going to the target system's ethernet port 1
- And another cable using the RX wires wired into the target's RX - this is going to the target system's ethernet port 2
So this quick first experiment proved that I might be onto something here, yet this was very fiddly. So, my first thought was to find some sewing needles which can be quick and stealthy.
Second Experiment

Time to try out some sewing needles. This time I soldered the listener's ethernet cable 1 RX wires onto the needles and then inserted them directly through the target's ethernet wires, using a piece of soldering iron foam to support them! The data is being passed through the sewing needles which is fascinating!

Exfiltrating the target's data packets
To receive both TX and RX from the target, I used an old mainboard which had two ethernet ports, I call this the "listening" machine. Why two ethernet ports? If I had a listening machine with one ethernet port, I could listen in on the target's RX only. If I wanted to exfil the target's TX I wouldn't be able to receive both on the listener's one RX feed. Therefore, the second ethernet port on the listener is used (via it's RX) to receive the target's TX transmission.
How to capture the target's packets? Wireshark of course! And the great thing about this tool is you can choose to capture on one or both of the listening machine's ethernet ports. If you wanted to just exfil the target's RX feed then you could just select one ethernet port.
Target's RX and TX
With Wireshark you can choose to capture an ethernet port in one window and other ports in other windows. Useful! Below you can see the target's HTTP requests and it's responses in the other window!
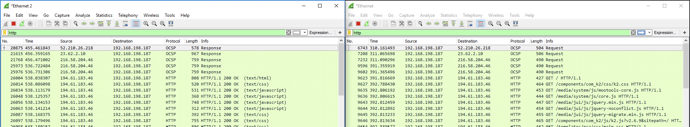
Or you can combine the two RX and TX feeds into one capture as seen below.
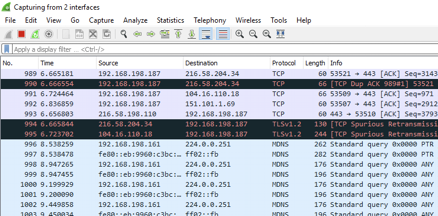
I think the target machine may have been slightly interrupted during insertion of the needles but overall it dropped little packets and I could see all of the HTTP requests (including everything else) that I was making on the target machine.

