Azure Sentinel: Querying for your Cyber Threat Indicators
All CTI entries aren't just available to view in the "Threat Intelligence" page - they are stored in the Log Analytics Workspace table "ThreatIntelligenceIndicator". Here you will find the manually submissions, but also any automated feeds from STIX/TAXII.

We've learnt how to manually add Threat Indicators to Azure Sentinel in another post, so what now?
All CTI entries aren't just available to view in the "Threat Intelligence" page - they are stored in the Log Analytics Workspace table "ThreatIntelligenceIndicator". Here you will find the manually submissions, but also any automated feeds from STIX/TAXII.
Head to your Log Analytics Workspace
Query for "ThreatIntelligenceIndicator" and you'll see every CTI added and these can be active or not.
If indicators are removed from the "Threat Intelligence" page in Sentinel it will not remove it from your CTI data. Instead it will be marked as active == false.
Hence, adding WHERE logic to only display active indicators.
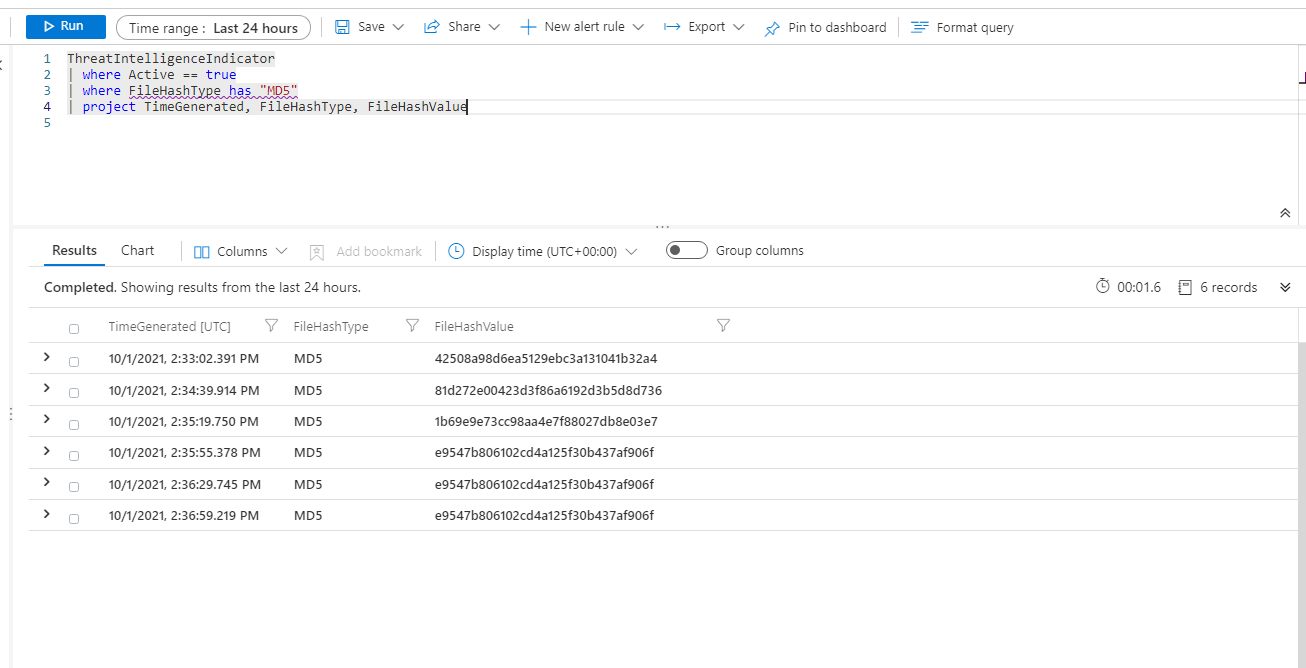
The CTI submissions from our previous post were all MD5 so here I've filtered it down further just to remove any other noise.
You'll get a lot of other fields, which may well be blank, so if you want to neaten up your results then you can pipe to "project" to pull out certain fields of interest.
// Query for Threat Indicators in Azure Sentinel
ThreatIntelligenceIndicator
| where Active == true
| where FileHashType has "MD5"
| project TimeGenerated, FileHashType, FilehashValueIt's simple as that. Of course when your indicators being to build up with varying types, such as domains and URLs, then your query's will become a lot more complex.
Check out the previous post on adding manual threat indicators @ https://www.cyber.engineer/azure-sentinel-adding-manual-threat-indicators/
